Did #GAP's Instagram get hacked? It's now posting #YZY designs after deleting all of its previous photos and making the YZY brand logo its… | Instagram
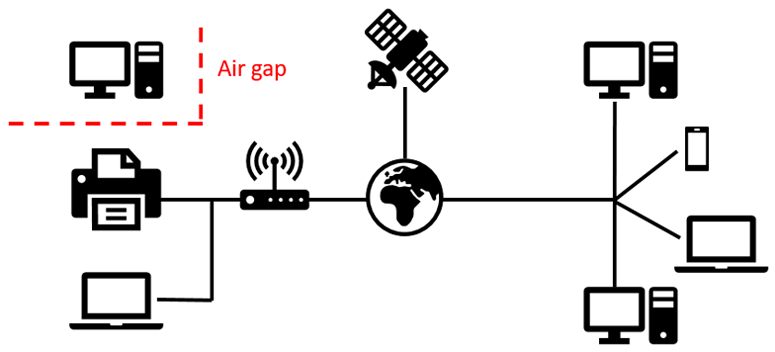
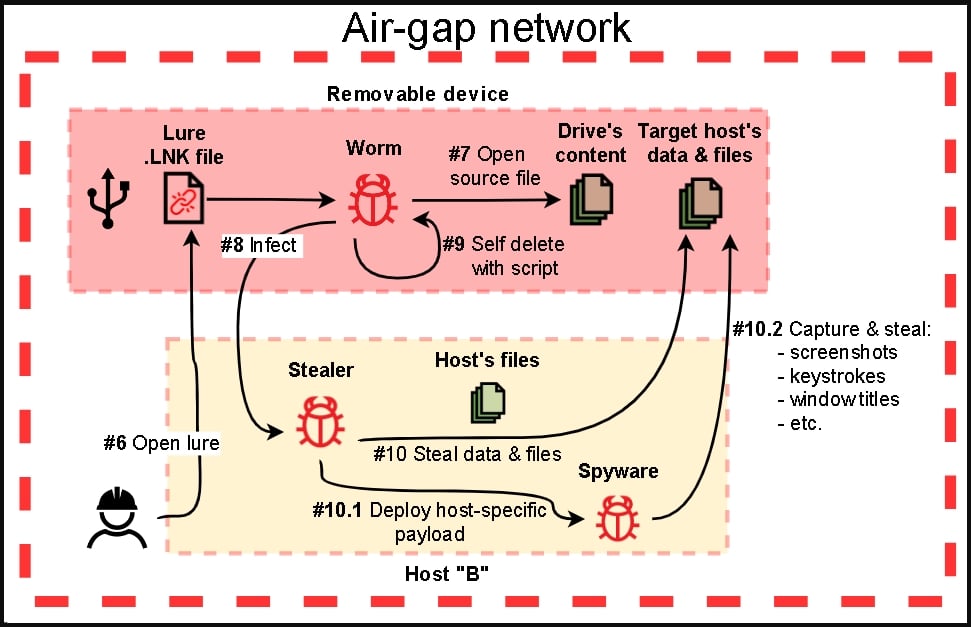
Hacking the Air Gap: Stealing Data from a Computer that isn't Connected to the Internet | Science Project

MIT CoLab on X: "Saturday: Join Boston neighbors, activists, archivists, and students who are #HackingTheArchive. We're hacking the racial wealth gap by exploring the strategies of past activists' whose actions can guide

Hacking the Air Gap: Stealing Data from a Computer that isn't Connected to the Internet | Science Project







![Using an Air-gapped Computer or Network in 2024 [Price & More] Using an Air-gapped Computer or Network in 2024 [Price & More]](https://www.cloudwards.net/wp-content/uploads/2022/02/Using-an-Air-Gapped-Computer-The-Best-Defense-Against-Hacking.png)