
Free Automated Malware Analysis Service - powered by Falcon Sandbox - Viewing online file analysis results for 'EFRService.exe'

Shiva v. N. Parasram - Digital Forensics With Kali Linux - Enhance Your Investigation Skills by Performing Network and Memory Forensics With Kali Linux 2022.x,-Packt Publishing (2023) | PDF | Computer Data Storage | Computer Forensics
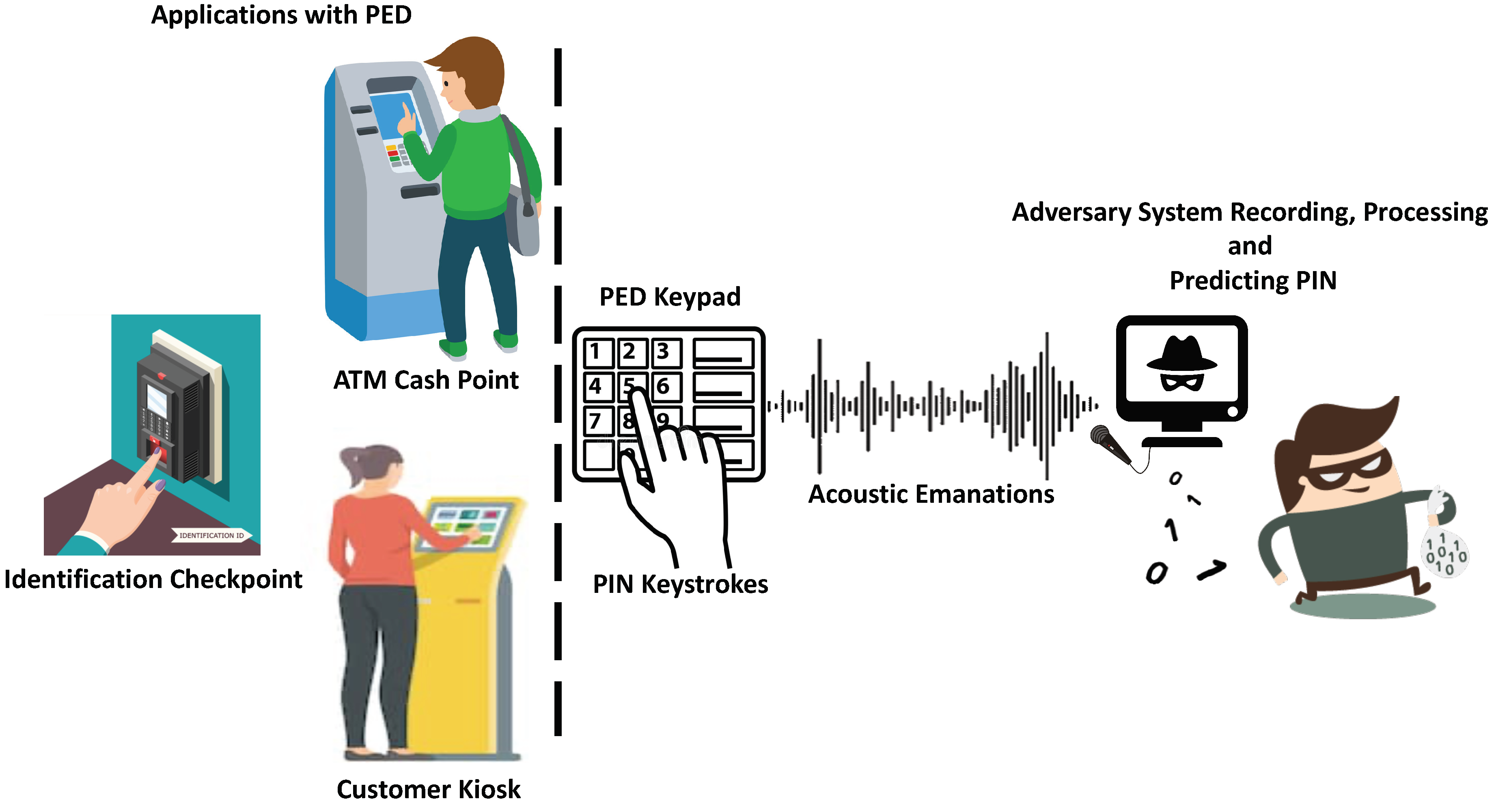
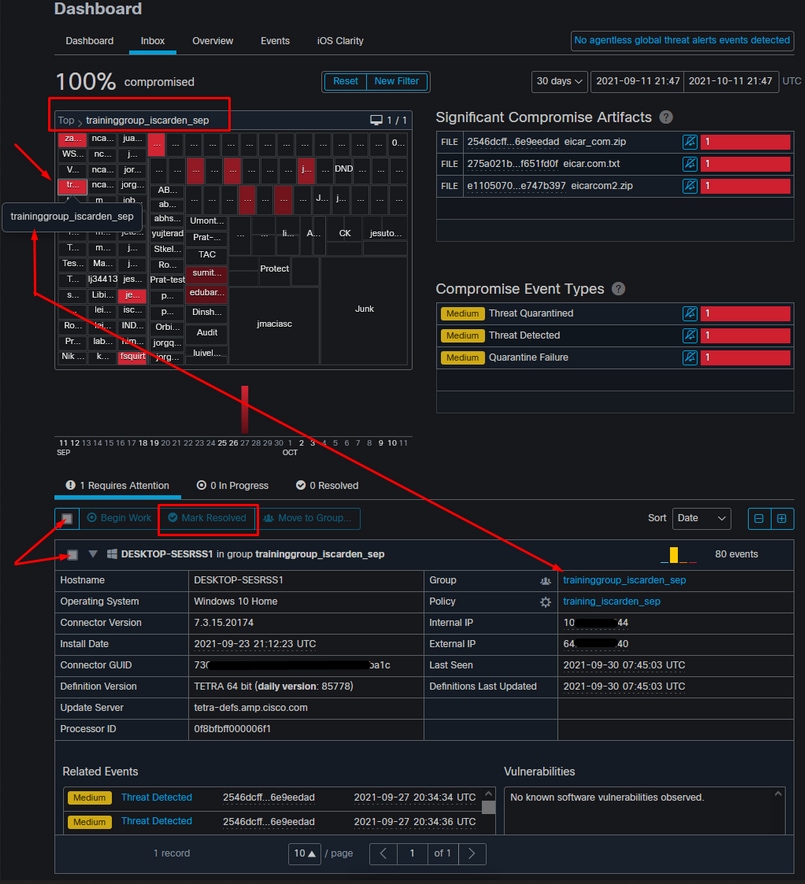
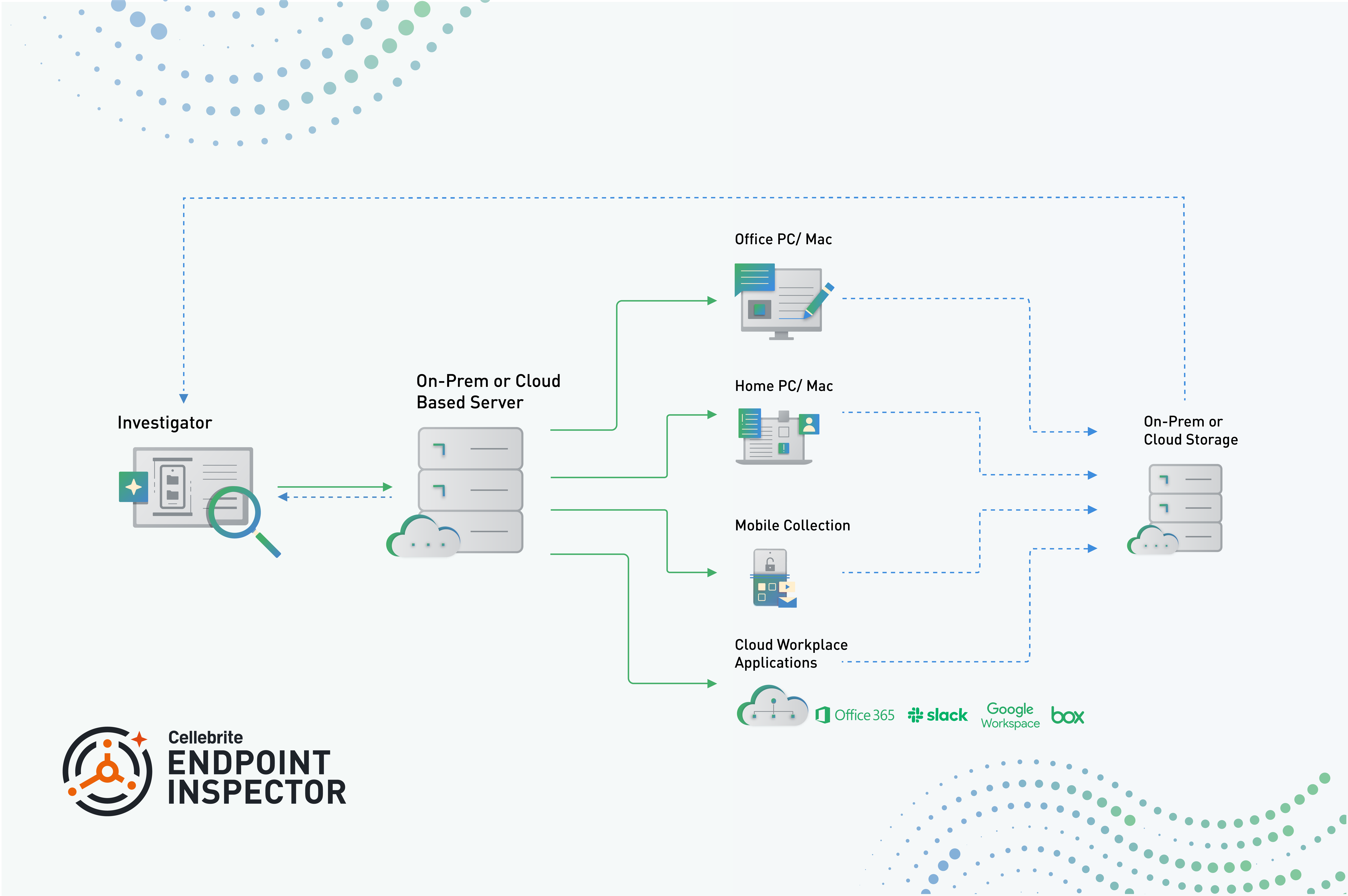

.jpg?width=1000&name=Symantec_Advanced_Threat_Protection_EDR(USE).jpg)





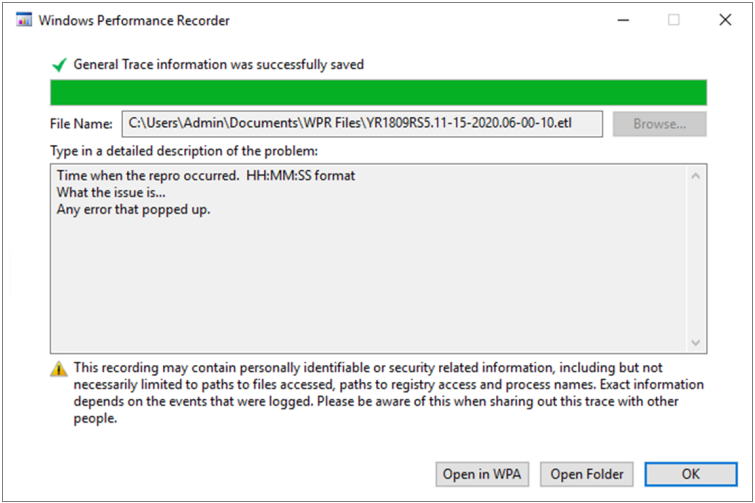

.jpg?width=1000&name=Microsoft_Defender_Endpoint(USE).jpg)



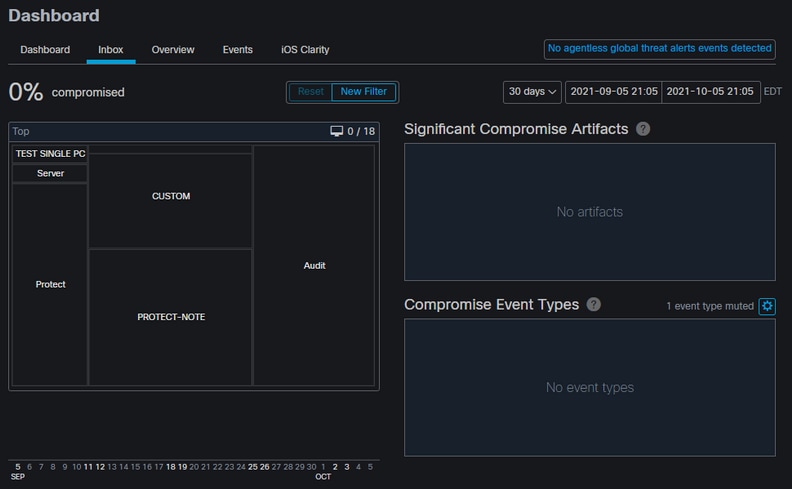
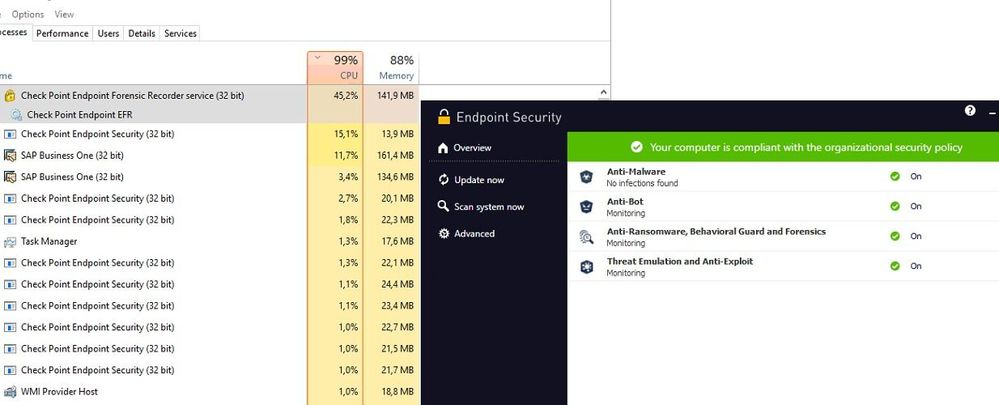
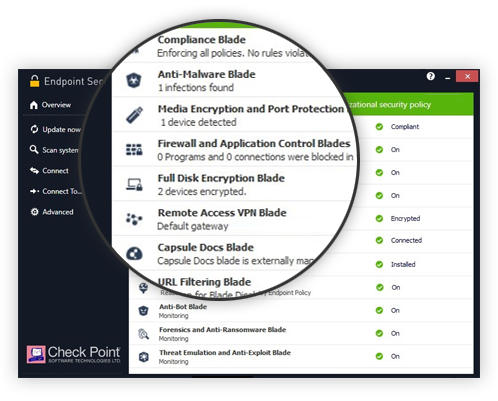
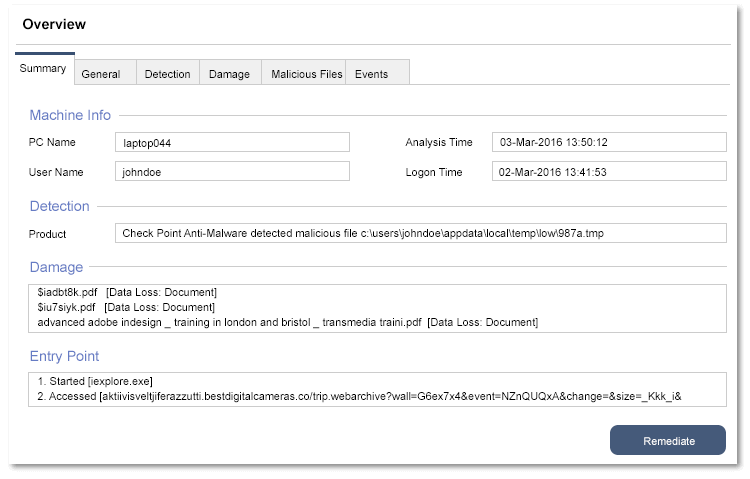
.jpg?width=1000&name=Check%20Point%20Harmony%20EDR%20(USE).jpg)