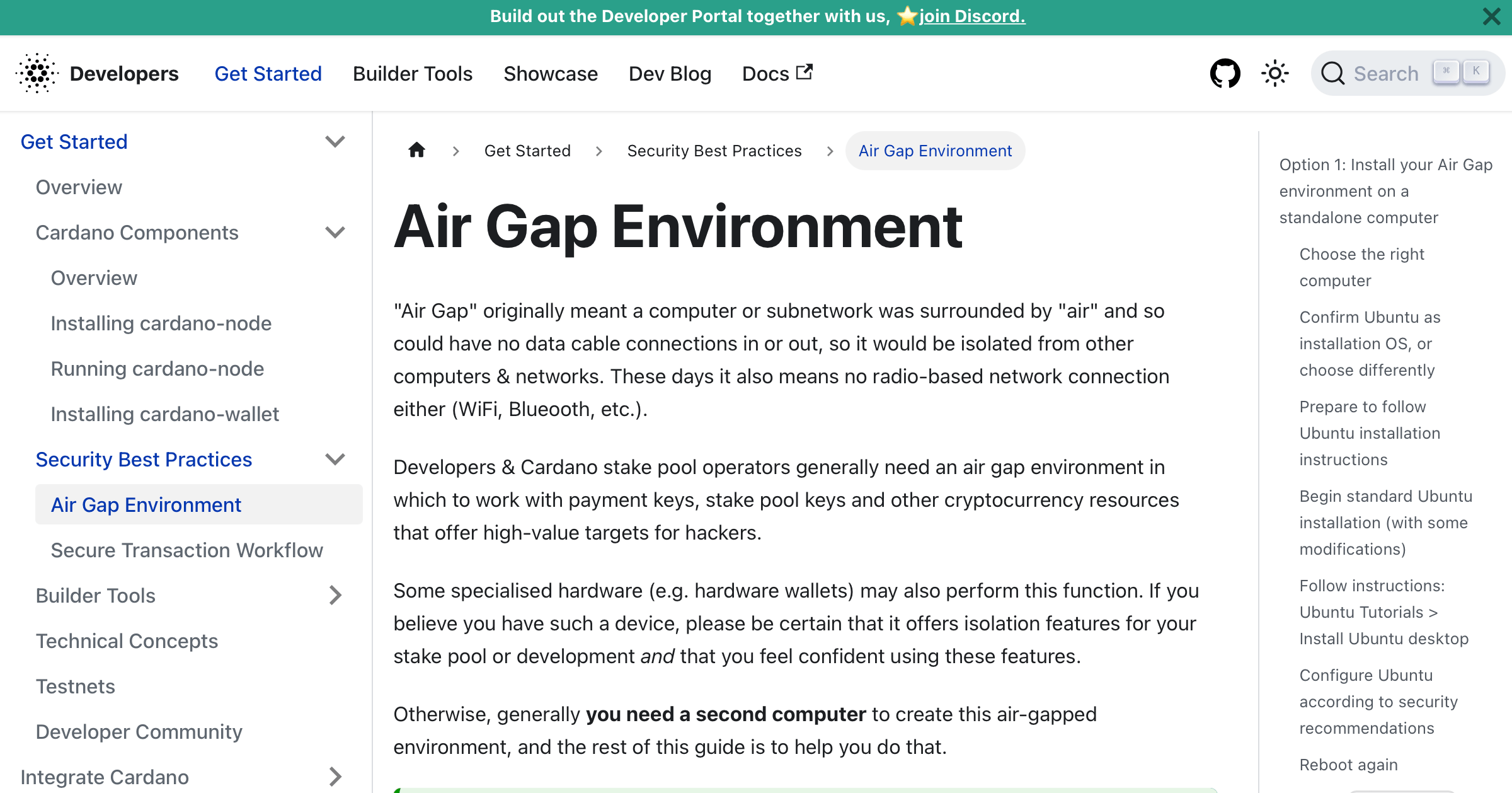
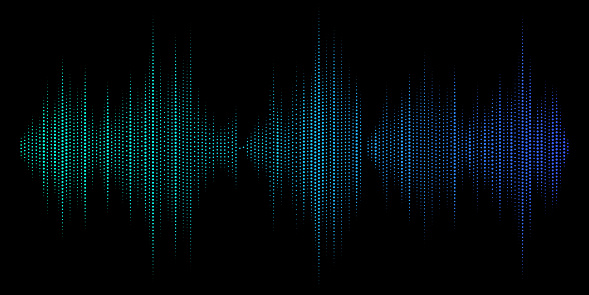
![CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT](https://image.slidesharecdn.com/v4a-161109044331/85/cb16-airgap-security-stateoftheart-attacks-analysis-and-mitigation-by-mordechai-guri-yisroel-mirsky-yuval-elovici-13-320.jpg?cb=1666823605)
CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT
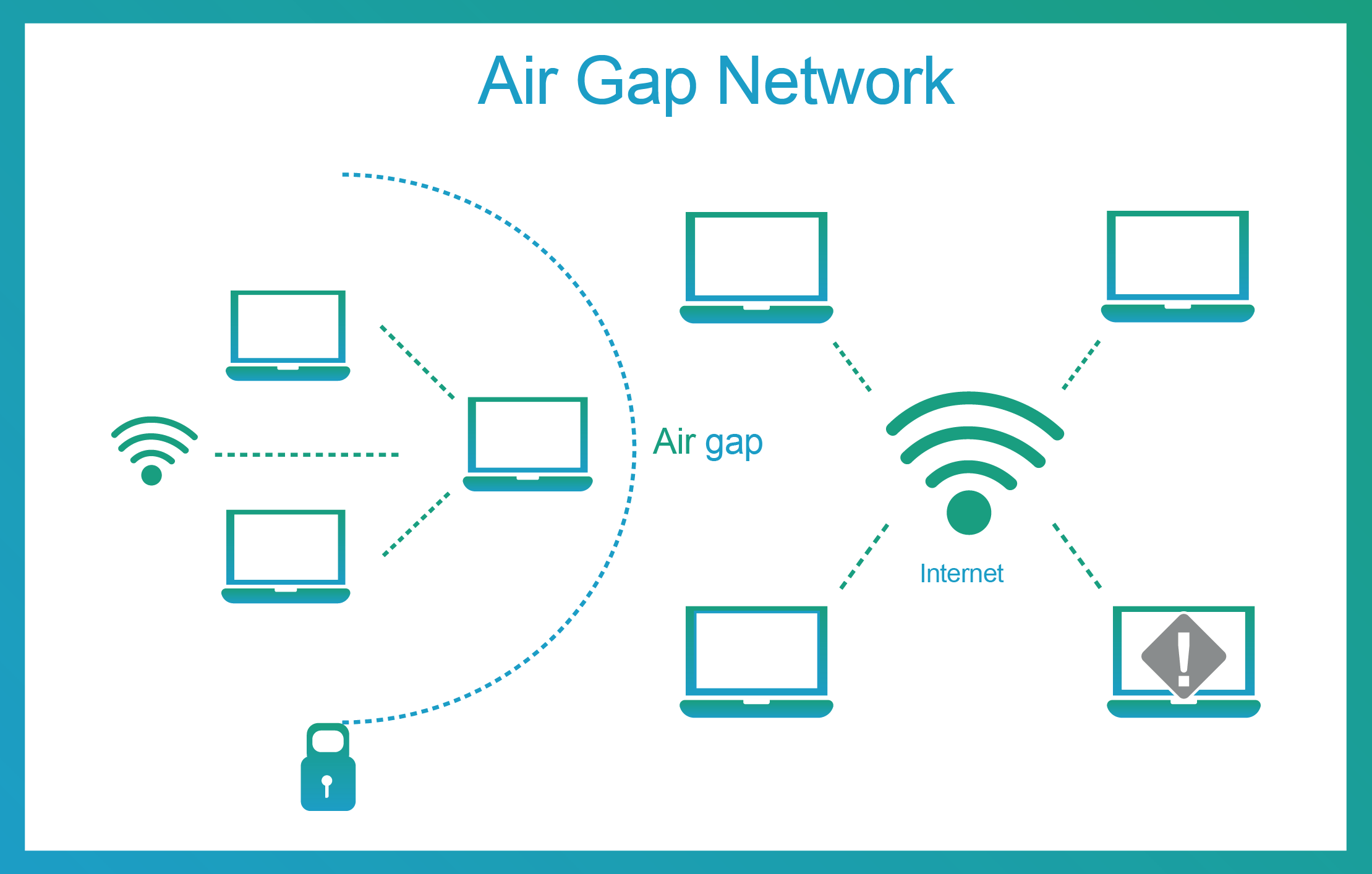
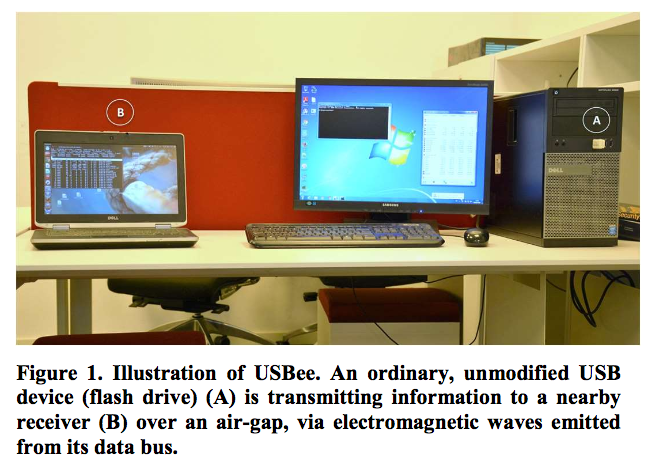
![CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT](https://image.slidesharecdn.com/v4a-161109044331/85/cb16-airgap-security-stateoftheart-attacks-analysis-and-mitigation-by-mordechai-guri-yisroel-mirsky-yuval-elovici-18-320.jpg?cb=1666823605)
CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT

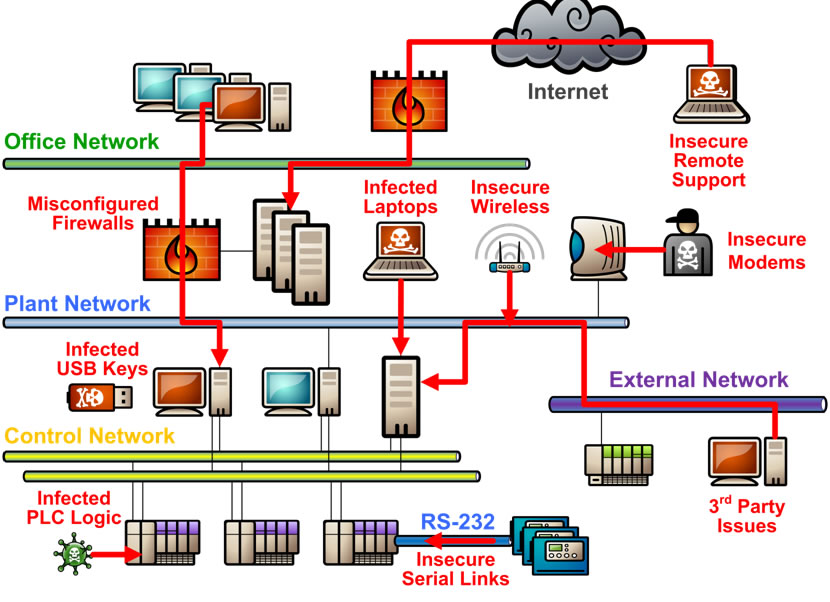
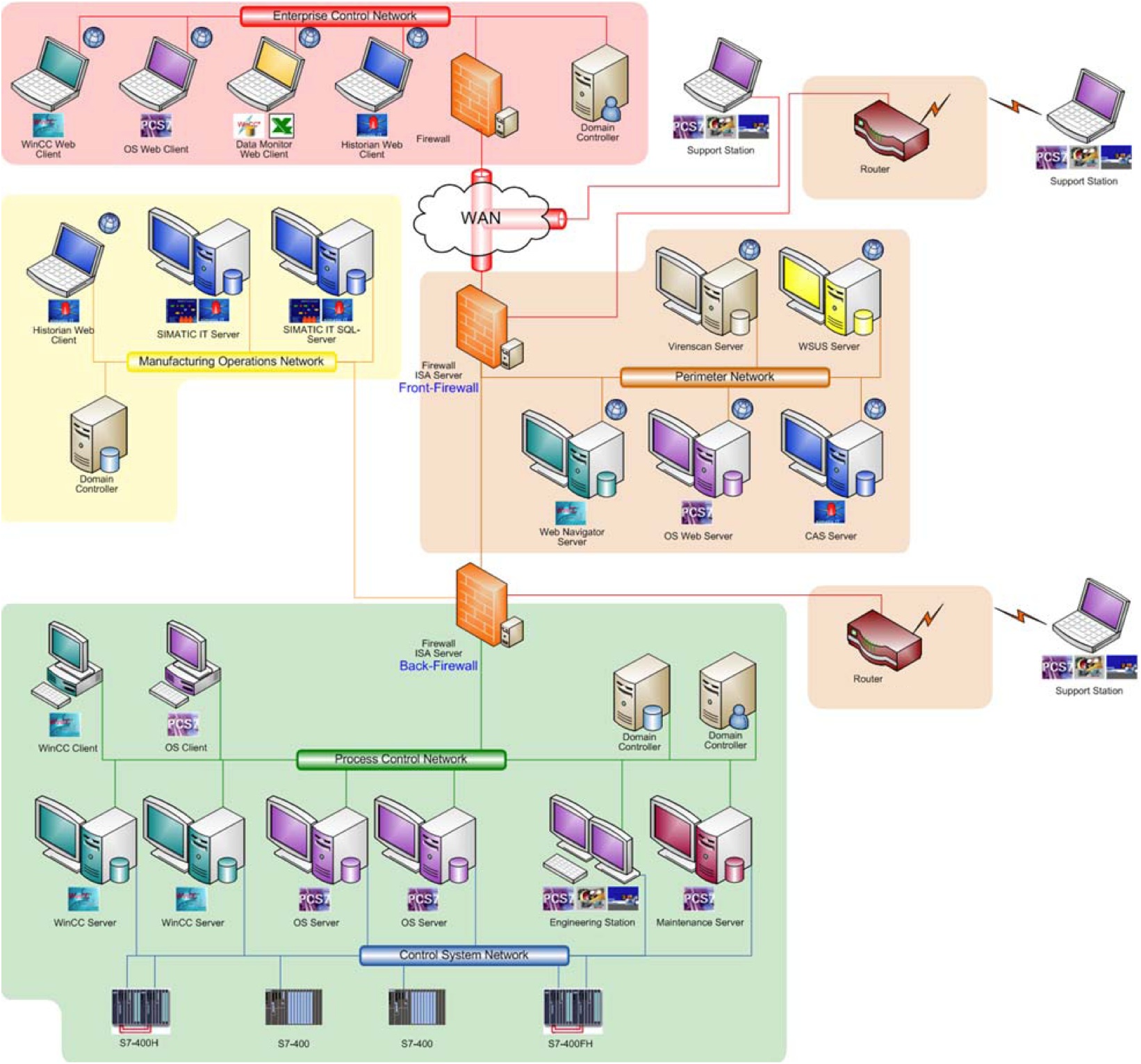
Design-based Fortifications | Cyber-security in Industrial Measurement and Control Systems | Textbook
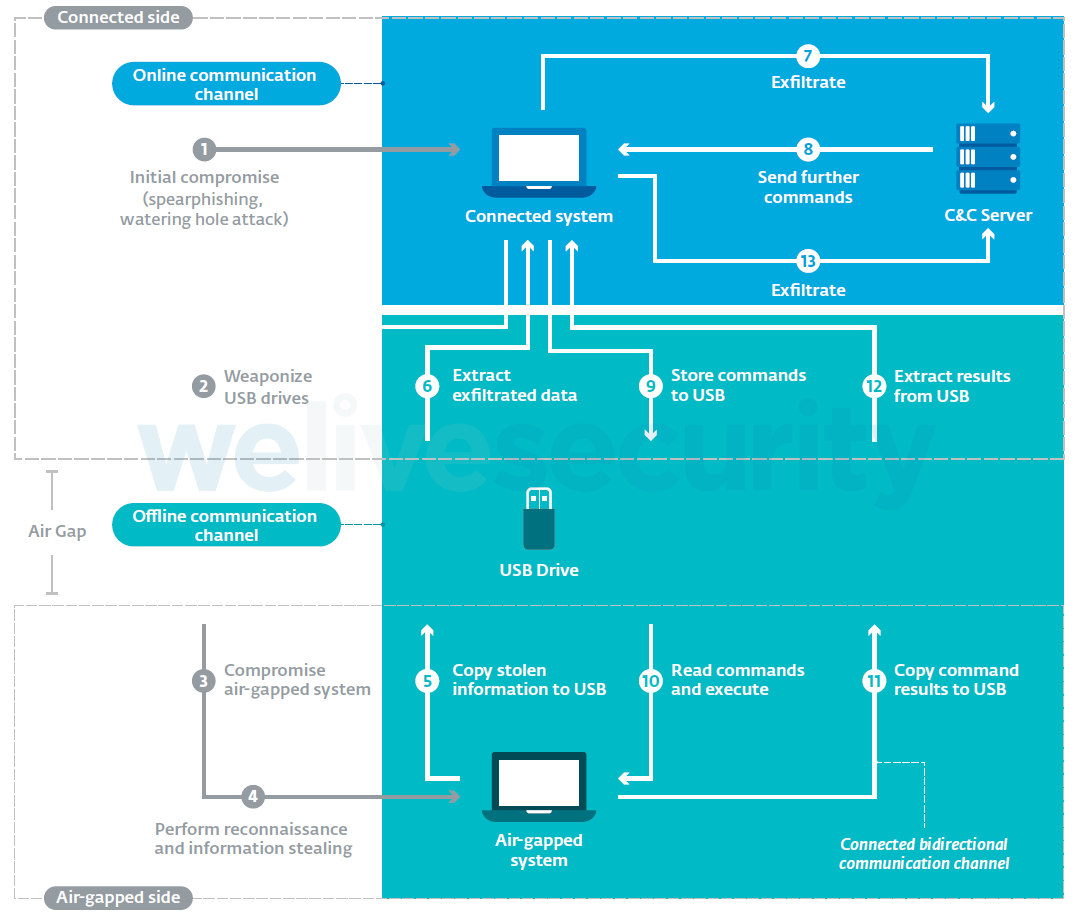
![CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT](https://image.slidesharecdn.com/v4a-161109044331/85/cb16-airgap-security-stateoftheart-attacks-analysis-and-mitigation-by-mordechai-guri-yisroel-mirsky-yuval-elovici-20-320.jpg?cb=1666823605)
CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT





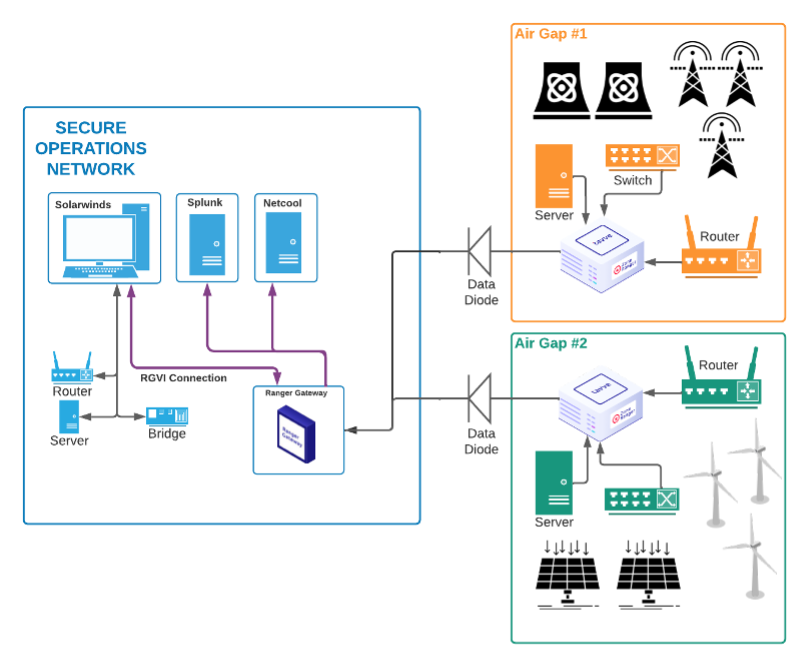
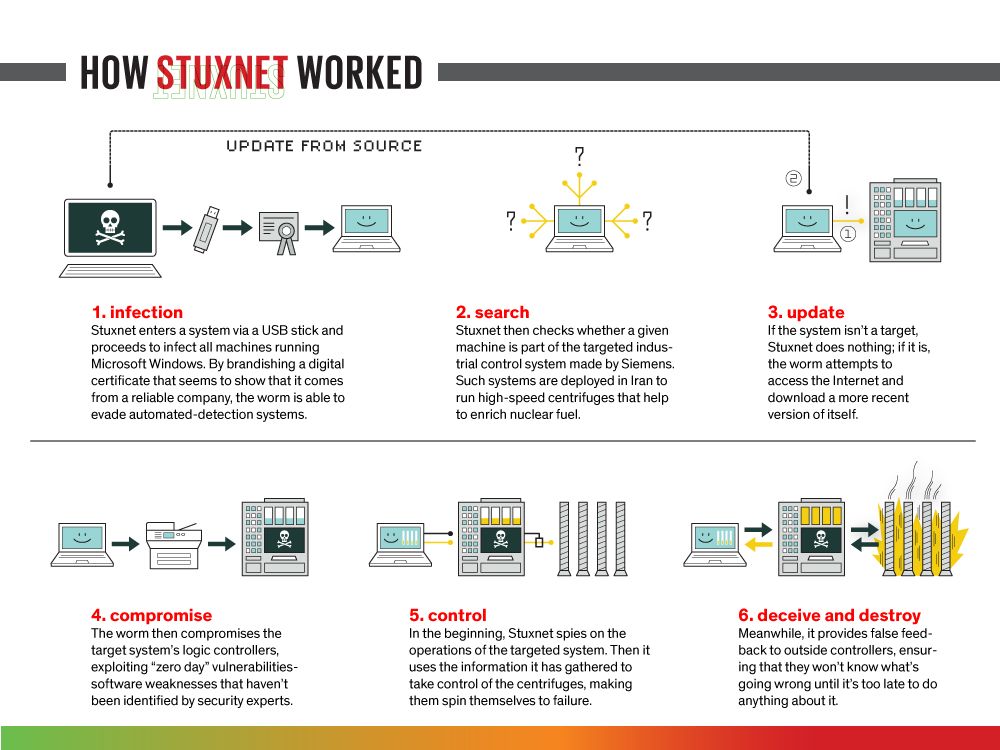

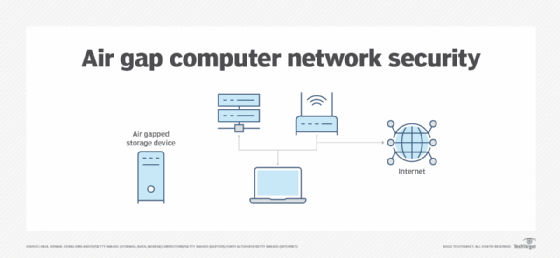

.png)